Explained — How Intel AMT Vulnerability Allows to Hack Computers Remotely
Earlier this week Intel announced a critical escalation of privilege bug that affects its remote management features shipping with Intel Server chipsets for past 7 years, which, if exploited, would allow a remote attacker to take control of vulnerable PCs, laptops, or servers.
The vulnerability, labeled CVE-2017-5689, affects Intel remote management technologies, including Active Management Technology (AMT), Intel Standard Manageability (ISM), and Intel Small Business Technology (SBT) software, versions 6 through 11.6.
The flaw was originally discovered by Maksim Malyutin, a member of Embedi research team, in mid-February, who then responsibly disclosed it to the Intel security team.
My previous article, published earlier this week, was based on the partial information shared by Maksim to The Hacker News, as the reported Intel AMT vulnerability was highly critical and can be exploited remotely, Embedi held technical details until most sysadmins update their systems with a patched firmware.
Today, Embedi research team has disclosed complete technical details about the critical vulnerability, revealing that a remote attacker can hijack computers powered by Intel Chipset just by sending an empty authentication string.
To understand how, I have compiled this piece explaining:
Intel-based chipsets come with an embedded technology, called Intel Active Management Technology (AMT), to enhance the ability of IT administrators, allowing them to remotely manage and repair PCs, workstations, and servers of their organization.
Using a web-based control panel, accessible from port 16992 and 16993, which comes pre-installed on the chipset, an administrator can remotely manage a system.
The Intel AMT Web Interface works even when the system is turned off, as long as the platform is connected to a line power and a network cable, as it operates independently of the operating system.
To protect Intel AMT Web Interface from unauthorized users, the service makes use of HTTP Digest and Kerberos authentication.
The escalation of privilege vulnerability resides in the way Intel AMT Web Interface handles user authentication over HTTP Digest protocol, which is based on a simple challenge-response paradigm.
The vulnerability, labeled CVE-2017-5689, affects Intel remote management technologies, including Active Management Technology (AMT), Intel Standard Manageability (ISM), and Intel Small Business Technology (SBT) software, versions 6 through 11.6.
The flaw was originally discovered by Maksim Malyutin, a member of Embedi research team, in mid-February, who then responsibly disclosed it to the Intel security team.
My previous article, published earlier this week, was based on the partial information shared by Maksim to The Hacker News, as the reported Intel AMT vulnerability was highly critical and can be exploited remotely, Embedi held technical details until most sysadmins update their systems with a patched firmware.
Today, Embedi research team has disclosed complete technical details about the critical vulnerability, revealing that a remote attacker can hijack computers powered by Intel Chipset just by sending an empty authentication string.
To understand how, I have compiled this piece explaining:
- What is Intel AMT technology?
- Where the Intel AMT Vulnerability resides?
- How can an attacker exploit Intel AMT Vulnerability?
What is Intel AMT technology?
Intel-based chipsets come with an embedded technology, called Intel Active Management Technology (AMT), to enhance the ability of IT administrators, allowing them to remotely manage and repair PCs, workstations, and servers of their organization.
Using a web-based control panel, accessible from port 16992 and 16993, which comes pre-installed on the chipset, an administrator can remotely manage a system.
The Intel AMT Web Interface works even when the system is turned off, as long as the platform is connected to a line power and a network cable, as it operates independently of the operating system.
Where the Intel AMT Vulnerability resides?
To protect Intel AMT Web Interface from unauthorized users, the service makes use of HTTP Digest and Kerberos authentication.
The escalation of privilege vulnerability resides in the way Intel AMT Web Interface handles user authentication over HTTP Digest protocol, which is based on a simple challenge-response paradigm.
Before going into the technical details about the exploitation of this vulnerability, first, you need to know how the Digest authentication works.
The Digest authentication completes in the following steps:
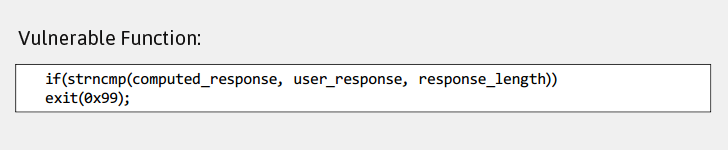
As, it’s obvious, for successful authentication, user_response variable must be equal to computed_response variable; hence the strncmp() function must return a zero value for any length.
But, according to the researcher, the programmers who coded this authentication process for Intel platform mistakenly used the length of the user_response variable in strncmp() function, instead of the computed_response variable for response_length parameter.
To exploit this logical flaw in Intel AMT Web Interface, all an unauthorized attacker needs to do is send nothing (null) into user_response to the server.
Since the strncmp() function is mistakenly using character length of the user_response variable to authorize the user, which in this case is null, the string comparison function would be tricked into matching nothing and believe that attacker's response (user_response) is equals to the computed_response.
As both variables matched, the attacker will be authenticated to log into the Intel AMT Web Interface and do whatever an authorized administrator can do, gaining high-level privileges on the system.
An attacker can also use Keyboard Video Mouse (KVM) feature, available inside Intel AMT Web Panel, which runs at a hardware level and allows sysadmins to remotely take control of the whole system, and perform tasks like:
The bug affects Intel manageability firmware versions 6.x, 7.x, 8.x 9.x, 10.x, 11.0, 11.5, and 11.6 for Intel's AMT, ISM, and SBT platforms. However, versions before 6 or after 11.6 are not impacted.
Intel has rated the vulnerability as highly critical and released new firmware versions, instructions to detect if any workstation runs AMT, ISM, or SBT, a detection guide to check if your system is vulnerable, and a mitigation guide for those organizations that can not immediately install updates.
So, the Intel customers are strongly recommended to install a firmware patch without wasting a single second.
Also, there's a simple mitigation tool available on Github, created by Malware researcher Bart Blaze, which is based on the Mitigation Guide provided by Intel.
All an affected user has to do is, just download and run DisableAMT.exe, it will disable Intel AMT on Windows operating system (x86 and x64).
The Digest authentication completes in the following steps:
- Client requests server to initiate login, and in response, the server returns a randomly generated 'nonce' value, the HTTP method, and the requested URI.
- Next, the user is prompted to enter his username and password.
- Once entered, the client machine sends an encrypted string (referred as user_response)—generated by applying a hash function to the entered username and password, server-supplied nonce value, HTTP method, and the requested URI—to the server.
- The server also calculates a similar encrypted string (referred as computed_response) using username and password stored in the database and all the other three values.
- The server compares both the strings using the strncmp() function and if they match, it allows the user to log into the Intel AMT Web Interface.
Syntax example:Strncmp() is a binary safe string comparison function that returns a negative, zero, or a positive integer depending upon whether string_1 is greater or less than string_2, and if they are equal, it returns zero.
strncmp (string_1, string_2 , length)
—where, length parameter defines how many characters needs to be compared.
As, it’s obvious, for successful authentication, user_response variable must be equal to computed_response variable; hence the strncmp() function must return a zero value for any length.
But, according to the researcher, the programmers who coded this authentication process for Intel platform mistakenly used the length of the user_response variable in strncmp() function, instead of the computed_response variable for response_length parameter.
How can an attacker exploit Intel AMT Vulnerability?
To exploit this logical flaw in Intel AMT Web Interface, all an unauthorized attacker needs to do is send nothing (null) into user_response to the server.
Since the strncmp() function is mistakenly using character length of the user_response variable to authorize the user, which in this case is null, the string comparison function would be tricked into matching nothing and believe that attacker's response (user_response) is equals to the computed_response.
As both variables matched, the attacker will be authenticated to log into the Intel AMT Web Interface and do whatever an authorized administrator can do, gaining high-level privileges on the system.
How Bad is this Vulnerability? Very Bad, Believe me.
An attacker can also use Keyboard Video Mouse (KVM) feature, available inside Intel AMT Web Panel, which runs at a hardware level and allows sysadmins to remotely take control of the whole system, and perform tasks like:
"[Attacker] can remotely load, execute any program to the target system, read/write any file (using the common file explorer)," the research team wrote in its paper [PDF]. "Using IDE-R (IDE Redirection), [the attacker] can remotely change the boot device to some other virtual image for example."
"Using SOL (Serial over LAN), [the attacker] can remotely power on/power off/reboot/reset and do other actions with this feature. Also, it can be used to access BIOS setup for editing," the team added.In short, a potential attacker can do everything that a sysadmin can do: he can log into a vulnerable machine's hardware, and silently perform malicious activities, like tampering with the system and installing virtually undetectable malware.
Install Firmware Update to Patch the Vulnerability NOW!
The bug affects Intel manageability firmware versions 6.x, 7.x, 8.x 9.x, 10.x, 11.0, 11.5, and 11.6 for Intel's AMT, ISM, and SBT platforms. However, versions before 6 or after 11.6 are not impacted.
Intel has rated the vulnerability as highly critical and released new firmware versions, instructions to detect if any workstation runs AMT, ISM, or SBT, a detection guide to check if your system is vulnerable, and a mitigation guide for those organizations that can not immediately install updates.
So, the Intel customers are strongly recommended to install a firmware patch without wasting a single second.
Also, there's a simple mitigation tool available on Github, created by Malware researcher Bart Blaze, which is based on the Mitigation Guide provided by Intel.
All an affected user has to do is, just download and run DisableAMT.exe, it will disable Intel AMT on Windows operating system (x86 and x64).










0 comments:
Post a Comment